
Computer security methods are designed to keep private things, well, private. There are many ways to secure a system. Some users use a simple username/password login scheme for basic protection. Other users may use extra protection through encryption in various ways like using VPN and disk encryption.
If you have sensitive client data on your machine (you might be running a business) or material deemed intellectual property or you are privacy cautious, you may want to consider disk encryption.
Some benefits of disk encryption are:
- Secure your system from hackers
- Prevent data leaks
- Protect you from potential liability issues
Disk encryption software prevents a desktop hard disk drive, a portable USB storage device, or laptop, from accessing unless the user inputs the correct authentication data. If your laptop is ever lost or stolen, encryption protects the data on the disk.
These days, new Windows-powered systems come with BitLocker encryption by default. On Linux, LUKS is the most popular way of employing disk encryption.
Wondering what is LUKS? I'll brief you on the topic.
Technical jargons
Before going further, some terms should be defined. There is a lot to LUKS so it will help to break things down, especially if you're beginning to look into this.
Volume: A volume is a logical storage area that can be used to store data. In the context of disk encryption, a volume refers to a portion of a disk that has been encrypted to protect its contents.
Parameters: Parameters are settings that control how an encryption algorithm works. Parameters might include the encryption algorithm used, the key size, and other details about how the encryption should be performed.
Cipher type: A cipher is a mathematical algorithm used for encryption It refers to the specific encryption algorithm that is being used to protect the data on an encrypted volume.
Key size: The key size is a measure of the strength of an encryption algorithm: the larger the key size, the stronger the encryption. It is often expressed in bits, such as 128-bit encryption or 256-bit encryption.
Header: The header is a special area at the beginning of an encrypted volume that contains information about the encryption, such as the encryption algorithm used and the encryption keys.
The next definition can be tricky to a newcomer, but it's worth knowing about, especially when dealing with LUKS; it's quite handy.
Container: A container is a special file that acts like a virtual encrypted volume. It can be used to store encrypted data, just like an encrypted partition. The difference is that a container is a file that can be stored on an unencrypted partition, while an encrypted partition is a portion of a disk that has been encrypted as a whole. A container, then, is a file that acts as a virtual encrypted volume.
What Is LUKS and What Can It Do?
Linux Unified Key Setup - LUKS is a disk encryption specification created by Clemens Fruhwirth in 2004 and was originally intended for Linux. It is a well-known, secure, and high-performance disk encryption method based on an enhanced version of cryptsetup, using dm-crypt as the disk encryption backend. LUKS is also a popular encryption format in Network Attached Storage (NAS) devices.
LUKS can also be used to create and run encrypted containers. Encrypted containers feature the same level of protection as LUKS full-disk encryption. LUKS also offers multiple encryption algorithms, several modes of encryption, and several hash functions - a little over 40 possible combinations.
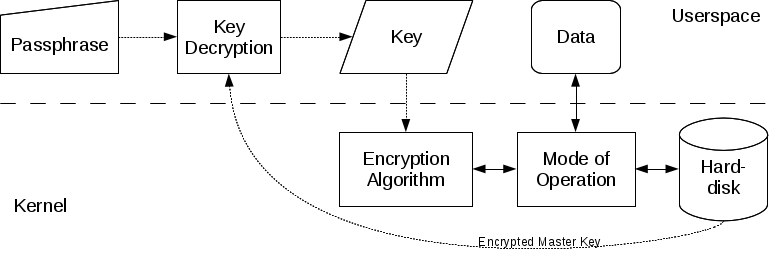
Any filesystem can be encrypted, including the swap partition. There is an unencrypted header at the beginning of an encrypted volume, which allows up to 8 (LUKS1) or 32 (LUKS2) encryption keys to be stored along with encryption parameters such as cipher type and key size.
The existence of this header is a major difference between LUKS and dm-crypt, since the header allows multiple different passphrases to be used, with the ability to change and remove them easily. It is worth a reminder, however, that if the header is lost or corrupted, the device will no longer be decryptable.
There are two versions of LUKS, with LUKS2 having features such as greater resistance to header corruption, and the use of Argon2 encryption algorithm by default (LUKS1 uses PBKDF2). Conversion between both versions of LUKS is possible in certain situations, but some features may not be available with LUKS1.
Where Can I Learn More?
I am hopeful that this short article is a help in understanding a little about LUKS and encryption. The exact steps for creating and using an encrypted partition with LUKS varies, depending on an individual's specific needs, so I will not cover installation and setup here.
If you want a guide to lead you though setting up LUKS, an excellent guide can be found in this article: Basic Guide To Encrypting Linux Partitions With LUKS. If you're new at this, and you want to try out LUKS, safe learning can be done on a virtual machine or a spare computer to get a feel for how it works.
from It's FOSS https://ift.tt/RvyF3Mr
via IFTTT
Tidak ada komentar:
Posting Komentar